The workshop will start on Wednesday, November 20 in the morning, and finish on Thursday, November 21 after lunch.
All the events, breaks and lunches will take place at the Couvent des Jacobins, the Rennes convention center.
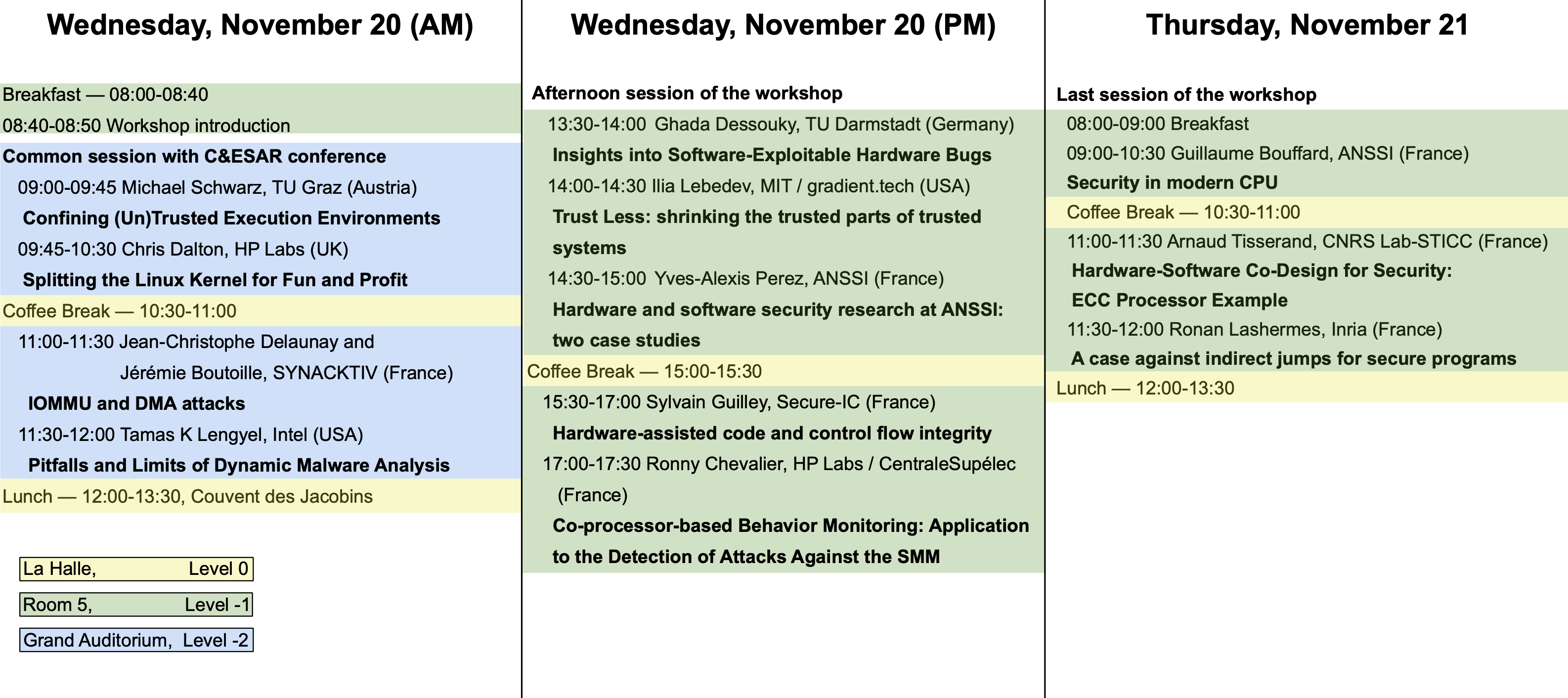
Wednesday, November 20
Morning — 08:00-12:00
Welcome session — 08:00-08:50, Room 5, Level -1
| 08:00-08:40 | Breakfast |
| 08:40-08:50 | Workshop introduction |
Session in common with C&ESAR conference — 9:00-12:00, Grand Auditorium, Level -2
| 09:00-09:45 | Michael Schwarz, Graz University of Technology (Austria) [slides] [video] Title: Confining (Un)Trusted Execution Environments Abstract: With Trusted Execution Environments, modern CPUs provide users with the possibility to isolate security-relevant applications from an untrusted system using so-called enclaves. Intel SGX is such a Trusted Execution Environment, which is supported on most Intel CPUs since around 2015. To prevent enclaves from harming the system, they run as unprivileged user code and are not allowed to execute any system calls.In this talk, we present the first practical enclave malware, which allows hiding arbitrary payloads, including zero-days, inside an enclave. This demonstrates that with the current hardware design, enclaves are a double-edged sword. They not only provide a way to protect trusted software, but they also give adversaries a powerful tool to hide malicious software with ready-to-hit exploits.We show that minimal changes to the SGX specification, which consider such scenarios, can fully prevent these attacks. As these changes require small changes in hardware or microcode, they are a long-term solution. As a short-term solution, we present SGXJail, a software mechanism to protect hosts from malicious enclaves. We show that our software confinement is compatible with existing enclaves while preventing a wide range of enclave malware threats in an efficient way. |
| 09:45-10:30 | Chris Dalton, HP Labs (UK) [slides] Title: Splitting the Linux Kernel for Fun and Profit Abstract: This talk looks at a pragmatic attempt at strengthening the security properties of Linux by introducing a degree of intra-kernel protection into the Linux kernel (supported by CPU Virtualization silicon features). Consider it, if you like, an attempt at retrofitting a ‘micro-kernel’ interface into traditionally monolithic Linux whilst maintaining a single Linux code base (yes it’s still Linux), no need for a hypervisor and with reasonable performance characteristics. The motivation for the work was the frightening increase in reliance on the security properties of the Linux kernel driven by trends away from full-virtualization solutions such as VMWare and KVM and towards lighter weight containment approaches led by Docker, et al for application hosting, deployment and consolidation. |
| 10:30-11:00 | Coffee break, La Halle, Level 0 |
| 11:00-11:30 | Jean-Christophe Delaunay and Jérémie Boutoille, SYNACKTIV (France) [slides] [video] Title: IOMMU and DMA attacks Abstract: This talk presents the current knowledge on Direct Memory Access attacks aiming to unlock a user logon session. The Input Output Memory Management Unit (IOMMU) functioning and its integration within the main operating systems (Windows, macOs and Linux) is firstly addressed in this presentation. Then, the existing DMA attacks using an external peripheral on a switched on computer are presented. These attacks give an access to a valid logon session even if the computer is locked. This research was performed in order to prepare the upcoming RAPID project by Synacktiv: DMArvest. |
| 11:30-12:00 | Dr. Tamas K Lengyel, Intel (USA) [slides] [video] Title: Pitfalls and Limits of Dynamic Malware Analysis Abstract: The presentation will cover a historic overview of the development of dynamic malware analysis systems, motivations behind it and the solutions developed over the years. The presentation will cover modern techniques to analyze malware using hypervisors, limitations of hypervisor introspection and modern sandbox evasion techniques used by malware. The presentation will conclude with a deep view into inherent computational limits of malware analysis and detail the problem with encoding assumptions about malware behavior that can be used to subvert the analysis process. |
Lunch — 12:00-13:30, La Halle, Level 0
Afternoon — 13:30-18:00, Room 5, Level -1
| 13:30-14:00 | Ghada Dessouky, TU Darmstadt (Germany) Title: Insights into Software-Exploitable Hardware Bugs Abstract: The recent outbreak of microarchitectural attacks has demonstrated to us how our trust assumptions in the underlying hardware of our systems are unjustified. Many performance optimization features in our modern processors, such as caches and speculative execution, have proven to exhibit security hazards that originate in the underlying microarchitecture, but can be exploited by means of software attacks. In this talk, we go even beyond the microarchitectural level and take a deep dive into the hardware designer’s perspective by reviewing state-of-the-art approaches used for security verification of hardware at design-time. We will show that a protection gap currently exists in detecting various classes of hardware bugs, many of which can be exploited by software-based attacks. Inspired by real-world CVEs and insights from our collaborators at Intel, we constructed the first representative testbed of real-world RTL security bugs based on RISC-V SoCs for the Hack@DAC competition we organized in 2018 and 2019. Based on our testbed, we conducted two case studies to analyze the effectiveness of state-of-the-art security verification approaches and identified specific classes of vulnerabilities which these approaches fail to detect. This talk will present some examples of these flaws and will shed light on the specific limitations of these approaches to propel future research in these directions. |
| 14:00-14:30 | Ilia Lebedev, MIT / gradient.tech (USA) [slides] Title: Trust Less: shrinking the trusted parts of trusted systems Abstract: Modern computers, industrial control systems, and other automation are broadly vulnerable as a result of decades of systemic forces that have prioritized cost and performance over correctness. Computers across the board face a crisis in the form of motivated software adversaries with access to our imperfect and enormously complex software. Considering these weaknesses, trust in modern computing systems is often not well-placed. Looking ahead to a shift in our collective priorities, this talk is centered around a rigorous discussion of hardware-assisted isolation and enclaves — authenticated software modules — as a means to drastically reduce the complexity of trusted systems. By allowing trustworthy enclaved software to co-exist with, but remain strongly isolated from, existing software, we enable a gentle transition toward trustworthy systems. Specifically, this talk describes a project refining formal definitions of enclaved execution and threat model via a series of hardware and software co-designs. These case studies explore enclave processors with small trusted computing bases spanning a gradient from an embedded SoC to a modern high-performance processor. This work is complementary to, and enables more effective application of, many powerful ideas such as information flow control, formal verification, multi-party computation, and other tools for trustworthy computing. |
| 14:30-15:00 | Yves-Alexis Perez, ANSSI (France) [slides] Title: Hardware and software security research at ANSSI: two case studies Abstract: At ANSSI, the hardware and software architecture lab is tasked with providing expertise to the various requesters on the low level software layers and high layers hardware ones: from operating system, kernel and hypervisors to hardware devices, and especially the interactions between them. After introducing the lab and the challenges it faces, the presentation will focus on two projects conducted recently: – WooKey, a research project which is both a hardened USB storage device and a framework for developing security-minded embedded projects – Hardware platform security requirements, an attempt to add security requirements to the hardware procurement process for the French administration and the test process developed for it |
| 15:00-15:30 | Coffee break, La Halle, Level 0 |
| 15:30-17:00 | Sylvain Guilley and Ritu-Ranjan Shrivastwa, Secure-IC (France) [slides] Title: Hardware-assisted code and control flow integrity Abstract: It is a safe point of view in cybersecurity to assume that software execution can be manipulated (through inputted “data”) and that bugs can be triggered (through “code” vulnerability activation). Furthermore, in the context of embedded systems, some more intrusive attacks (e.g., fault attacks) can be perpetrated, such as data corruption and control flow modification, such as instruction skips.In this context, the assistance of hardware to safeguard the application runtime execution is emerging as a key requirement. Several approaches exist: to name a few, fat pointers, low-fat pointers, basic block signature, destination whitelists, etc. Those solutions can come with various advantages (speed, coverage, etc.) and drawbacks (intrusiveness, non-determinism, etc.).In this tutorial, we will review those approaches, and also introduce Cyber Escort Unit, a portable “Code and Control Flow Integrity” solution, which does not interfere with the core and which feature predictable latency. Cyber Escort Unit will be demoed on a RISC-V core, within Secure-IC Securyzr embedded secure element. |
| 17:00-17:30 | Ronny Chevalier, HP Labs and CentraleSupélec (FR) [slides] Title: Co-processor-based Behavior Monitoring: Application to the Detection of Attacks Against the System Management Mode Abstract: Highly privileged software, such as the BIOS, is an attractive target for attackers. Thus, BIOS vendors use cryptographic signatures to ensure firmware integrity at boot time. Nevertheless, such protection does not prevent an attacker from exploiting vulnerabilities at runtime. This talk will present our approach, previously published at ACSAC, to detect such attacks. In particular, we apply this approach to detect attacks targeting the System Management Mode (SMM), a highly privileged x86 execution mode executing firmware code at runtime. We will present how we model the behavior of SMM code, how we gather information about its behavior, and how we ensure the integrity of our models despite the privileges of the SMM. Finally, we will present our simulation-based prototype and our experimental results. |
Thursday, November 21
Morning — 8:00-12:00, Room 5, Level -1
| 08:00-09:00 | Breakfast |
| 09:00-10:30 | Guillaume Bouffard, ANSSI (France) [slides] Title: Security in modern CPU Abstract: Modern CPUs are daily use in our smartphone and several IoT devices. These components compute more and more sensitive data. However, they are only designed to prevent software attacks. Recently, few publications focus on breaking modern CPUs from hardware layout. In this presentation, we will see how hardware security in modern CPU is also important than software security and why should be take in account. |
| 10:30-11:00 | Coffee break, La Halle, Level 0 |
| 11:00-11:30 | Arnaud Tisserand, CNRS Lab-STICC (France) [slides] Title: Hardware-Software Co-Design for Security: ECC Processor Example Abstract: Designing accelerators or blocks for security and cryptography in hardware usually leads to mode efficient and secure solutions than pure software implementations. But this can also lead to a flexibility problem: e.g. limited updates and adaptation to various security levels. We will present some ideas and results on the design of cryptoprocessors mixing hardware efficiency (speed, energy and security) and software flexibility in the case of elliptic curve cryptography for embedded systems. |
| 11:30-12:00 | Ronan Lashermes, Inria (France) [slides] Title: A case against indirect jumps for secure programs Abstract: A desired property of secure programs is control flow integrity (CFI): an attacker must not be able to alter how instructions are chained as specified in the program. Numerous techniques try to achieve this property with various trade-offs. But to achieve fine-grained CFI, one is required to extract a precise control flow graph (CFG), describing how instructions are chained together. Unfortunately it is not achievable in general. In this presentation, we propose a way to overcome this impossibility result by restricting the instruction set architecture (ISA) semantics. We show that forbidding indirect jumps unlocks a precise CFG extraction for all acceptable programs. We discuss the implications and limitations of the new semantics and argue for the adoption of restricted ISAs for security-related computation. |
Lunch — 12:00-13:30, La Halle, Level 0